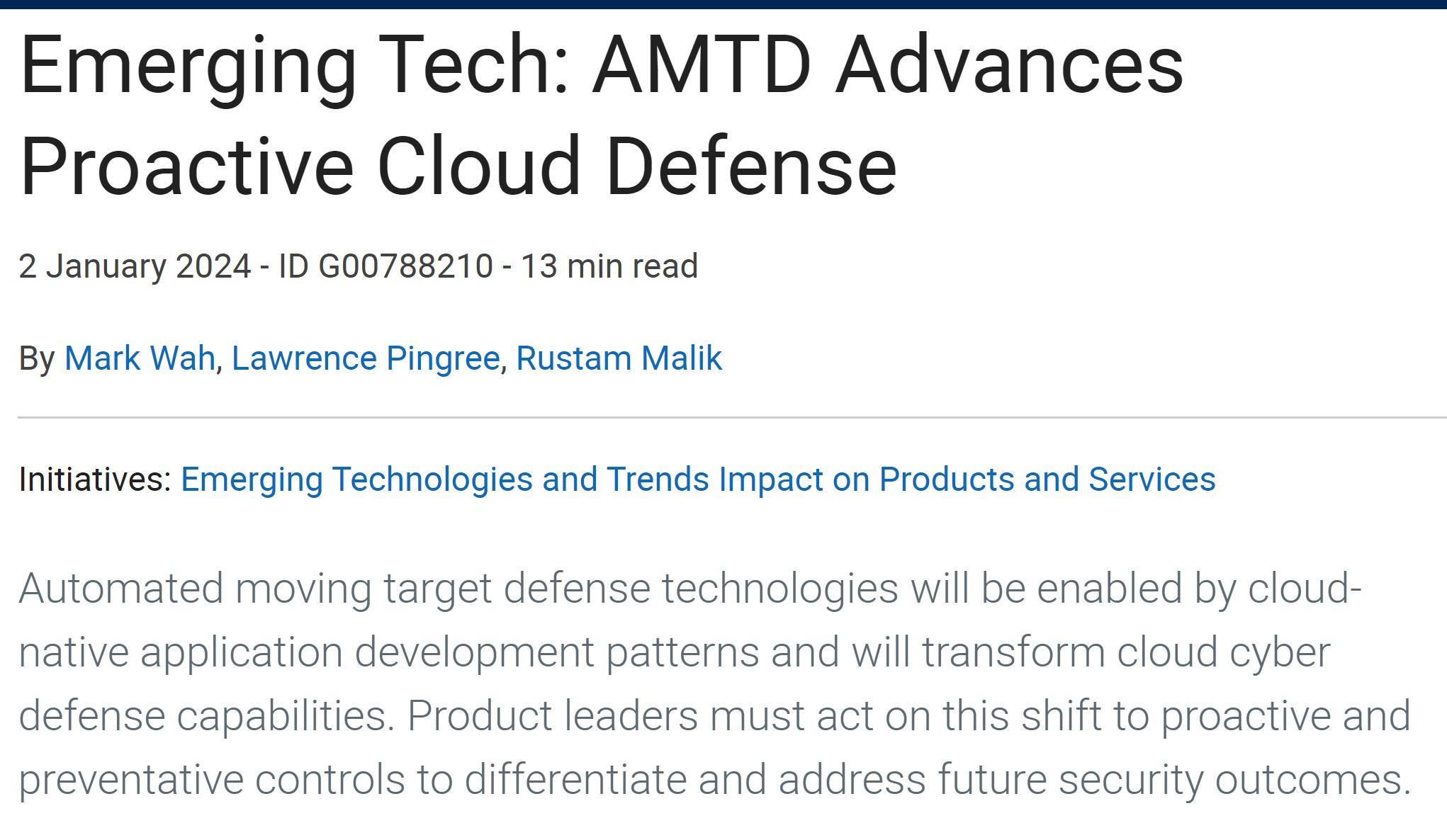
Hopr's Workload Security Proxy (WoSP) offers unparalleled protection for your containerized applications, APIs, and data. With our Automated Moving Target Defense, you can ensure secure and trusted access for every communication session.
The Hopr WoSP is the 'building block' to achieve Zero Trust, quantum-proof, application networking across all cloud environments. It shrinks and animates the enterprise attack surface using Runtime Microsharding™ and protects each shard with an
Automated Moving Target Defense (AMTD).
Runtime Microsharding™ is a novel Hopr mechanism that breaks a large attack surface into many small pieces (microshards) and animates them to make them appear as a mirage to attackers. What they think is accessible disappears when they try to reach it.
Hopr's WoSP rapidly 'hops' the access credentials for containerized apps to disrupt a threat actors ability to find and misuse them. Only trusted applications can know the correct credentials to gain access.
Hopr's WoSP manages a dynamic Machine Identity credential (a MAID™) that is issued with high trust, is repeatedly verified for trust at each communication session, and builds a chain of trust in workloads and machines.
Hopr's WoSP enables seamless application networking across clouds with comprehensive, end-to-end-encrypted communication channels (without exposing a key in an exchange).
WoSPs are small, lightweight, networking proxies that incorporate three unique and patented security technologies and protocols
CHIPS™ technology uses an algorithm to generate a cryptographic secret. The magic of CHIPS is that two identically configured WoSPs can generate an identical secret if their algorithms run at nearly the same time.
The SEE™ protocol uses the CHIPS™ secret to build an end-to-end-encrypted communication channel at the start of a communication session between two WoSPs, eliminating the vulnerability of a key exchange.
A MAID™ is a decentralized dynamic machine identity credential that is issued by a Hopr control plane, identity provider, and trust verifier.
The MAID™ is managed and rotated by the WoSP and verified for trust by an external Trust Verifier at the start of each communication session .
In runtime, the AMTD breaks the attack surface into very small shards and makes it nearly impossible for threats to recon, map, and attack. A new AMTD is formed around pairs of workloads and devices each time they communicate.
Our patented CHIPS™ technology enables rotation of credentials at a high frequency to create a moving target defense that prevents threat actors from gaining the information they need for an attack.