Hopr Korvette-SE
The WoSP for Multi-cloud


“The Kerberos security pattern is well-proven. What Hopr has developed is a novel implementation of Kerberos that will enhance the protection of cloud workloads.”
Senior Director, Global Technology Analyst
Secure East-West and North-South traffic with a zero trust
automated moving-target defense
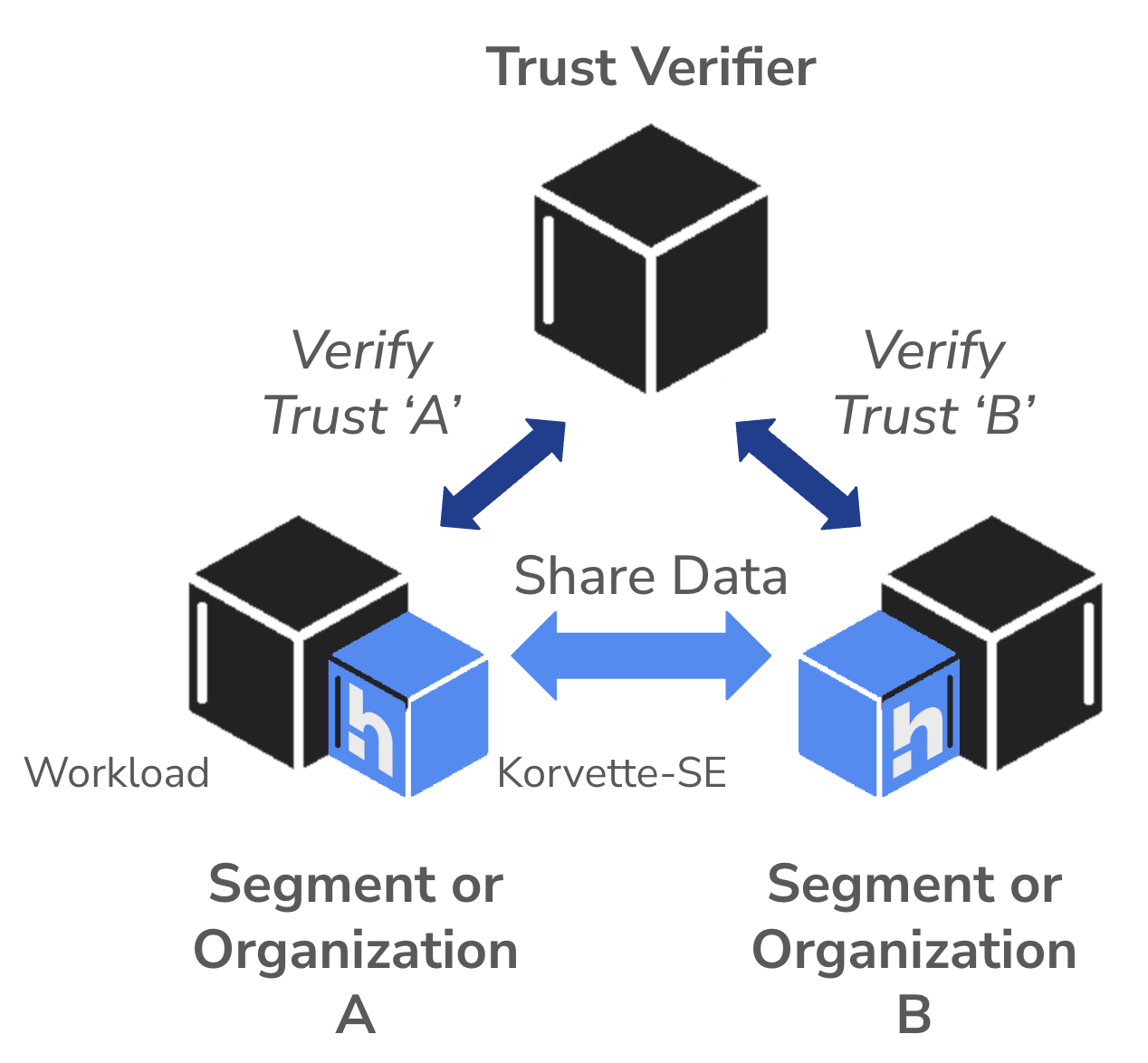
When a Korvette-SE WoSP needs a session with a third party Korvette-SE WoSP (outside of its home environment), the initiating Korvette-SE sends an encrypted message to Hopr's Trust Verifier, requests a session, and identifies the other workload.
The Hopr Trust Verifier decrypts the initiating WoSP's message, verifies its MAID™, and learns the identity of the second workload. If initiator's identity trust is verified, the Trust Verifier provides the initiating Korvette-SE with a one-time CHIPS™ algorithm ID for the requested session.
Upon receiving the one-time CHIPS™ algorithm ID from the Trust Verifier the initiating Korvette-SE WoSP generates a key and encrypts its first message to the second Korvette-SE WoSP and sends it to that WoSP.
Upon receipt of an encrypted message from the initiating WoSP, the receiving Korvette-SE WoSP communicates with the Trust Verifier and identifies the initiating WoSP. The Trust Verifier verifies the MAID™ credential of the second WoSP and provides it with the same one-time CHIPS™ algorithm ID.
The second Korvette-SE WoSP runs the one-time CHIPS™ algorithm and decrypts the message from the initiating Korvette-SE. Both WoSPs use their identical keys (from the one-time CHIPS™ algorithm ID) for their direct peer-to-peer session until either party closes the session, at which time the keys and CHIPS™ algorithm ID vanish.

Yes. When using Korvette-SE WoSPs at any edge, wether it is a cluster, cloud, or domain, the Korvette-SE WoSP can only trust and communicate with a Korvette-SE WoSP at the edge of the other environment.
Yes. The 'Kerberos for the Cloud' protocol ensures that the high trust and hardened data communications are the same for internal and external workload connections.
The Korvette-SE acts as a gateway between Korvette-SE WoSPs that communicate securely with external workloads and Korvette-S WoSPs that communicate with trusted internal workloads. The 'sidecar' portion of the Korvette-SE must be configured identically to the Korvette-S sidecar WoSPs that are deployed in the cluster, segment, cloud, or domain where the Korvette-SE is deployed.

