In the world of enterprise architecture, there is a promise that has been sold to technical leaders for the better part of a decade: the promise that Digital Transformation will bring Cloud Native utopia. It’s a vision where microservices spin up and down effortlessly, where deployment velocity is measured in minutes, and where resilience is inherent.
But if you walk into the average war room of a digital enterprise today, the reality looks different. We see DevOps teams drowning in YAML files. We see security architects trying to reverse-engineer firewall rules for ephemeral containers that lived for only thirty seconds. We see SOCs overwhelmed with attack activity, false positives, and stress. We see a landscape where the complexity of running the application has vastly outstripped the complexity of writing the application.
The traditional Software Development Lifecycle (SDLC) is hitting a wall, not because the code is bad, but because our approach to connecting that code is backwards. We are trying to build the plane while flying it, adding security and networking as afterthoughts to business logic.
Lane7 blueprints propose a radical, yet intuitive shift: flip the script. Build the network first. Secure the pathways first. Then, and only then, drop in the logic.
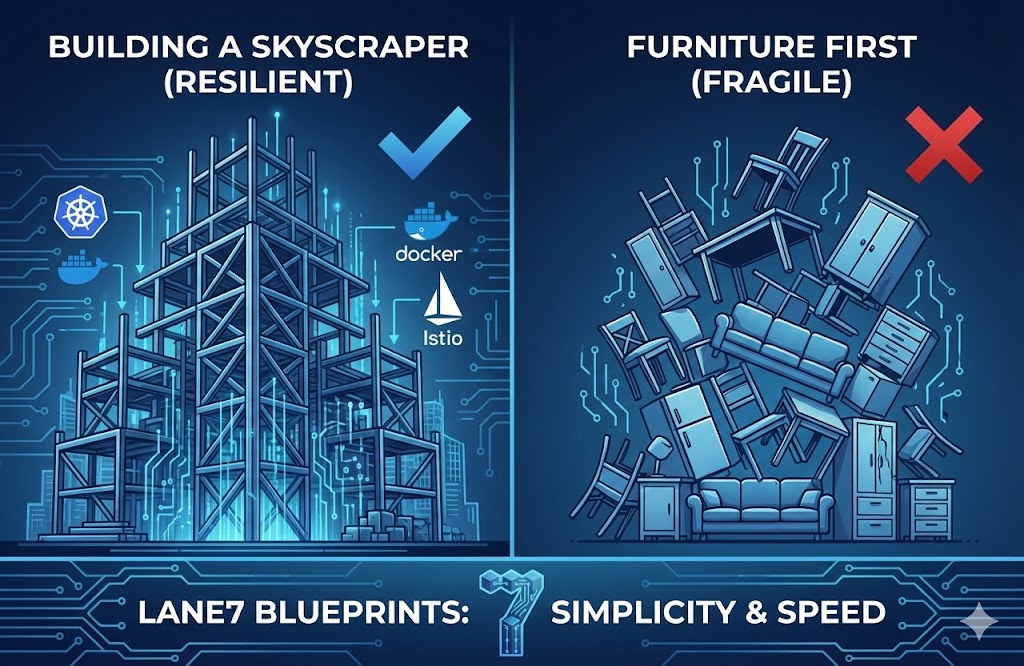
The "Furniture First" Fallacy
To understand why the current model is failing, we need to look at how we currently build cloud applications.
Imagine you are tasked with building a modern, high-security office skyscraper. In the physical world, the process is strictly ordered. You dig the foundation, you erect the steel frame, you install the HVAC, the electrical wiring, and the security checkpoints. Only when the environment is safe, powered, and connected do you invite the tenants to bring in their desks and computers.
In the current software development lifecycle, we do the opposite. We ask developers to build the "furniture"—the application logic, the databases, the shopping carts—first. They build these components in isolation on their laptops. Then, we put these components into the hands of DevOps and Platform Engineers who push the apps to the cloud (the "construction site") while trying to build the walls and wiring around them before the next component versions arrive..
We attempt to stitch these disparate pieces of code together using complex overlay networks. We struggle to wrestle Kubernetes configurations into submission and live through “YAML Hell”. We try to implement a Service Mesh like Istio to manage traffic, only to realize that configuring the mesh requires more engineering hours than writing the original app.
This is the "Furniture First" fallacy. We are deploying business logic into a vacuum and scrambling to build the infrastructure around it before the first packet arrives. The result? Misconfigurations, gaping security holes, and a deployment process that crawls at a snail's pace.
The Complexity Trap: Kubernetes, Docker, and the Mesh
For the security architect, this chaos is the stuff of nightmares.
In a monolithic era, we had a perimeter. We trusted IP addresses, subnets, and ports. This worked when servers were physical boxes that didn't move. We knew where the door was. In a microservices environment powered by Docker and Kubernetes, the perimeter has dissolved. Every service talks to every other service. The "network" is no longer cables and switches; it is a sprawling, invisible web of API calls.
To manage this, the industry invented tools of immense power and immense complexity. Kubernetes is the operating system of the cloud, but it demands a steep learning curve. Service meshes were introduced to handle the "dial tone" between services, but they introduced their own heavy operational tax. A lot more complexity was happening at Layers 3 and 4 of the OSI model.
But in a cloud-native environment the infrastructure is ephemeral. Containers spin up and die in seconds. Their IP addresses change constantly. Trying to apply Layer 3/4 security rules (like "Allow IP 10.0.0.1 to talk to 10.0.0.2") to a dynamic environment is a losing battle. It forces developers to become network engineers, managing CIDR (Classless Inter-Domain Routing) blocks, port collisions, and routing tables.. This is the hidden source of complexity: we are trying to force modern applications into legacy networking constructs.
The effort required to configure deployment manifests, ingress controllers, sidecar injections, and mutual TLS (mTLS) certificates often dwarfs the effort of writing the actual code. We have turned developers into amateur network engineers, asking them to understand CIDR blocks and certificate rotation when they should be focused on feature velocity.
This complexity is the enemy of security. Complexity hides vulnerabilities. It obscures visibility. And most importantly, it slows down the very agility the cloud was supposed to provide.
The Lane7 Paradigm: The Steel Frame Approach
Lane7 blueprints introduce a methodology that returns sanity to the process: Application Network First.
As the name implies, Lane7 operates strictly at Layer 7 (the Application Layer). By abstracting the network up to the application level, we stop caring about IP addresses and ports. We start caring about Identity and Services using a true Zero Trust for Workloads approach..
Before a single line of business logic is deployed, Lane7 defines the "steel frame" of the application. A Lane7 blueprint is a pre-constructed architectural pattern. It is a reusable, adaptable model that defines how services should connect, who should talk to whom, and how those conversations are secured.
Think of a Lane7 blueprint as a "Smart Skyscraper" kit. It comes with the steel frame erected, the electricity wired, the security cameras active, and the ID card scanners installed at every door. It creates a sterile, secure vacuum.
The network architecture, the access controls, the authentication, and the authorization are pre-configured. The "plumbing" of Layers 3 and 4 is irrelevant because of the method of abstraction.
This allows the DevOps or Platform Engineer to treat the network as a utility, not a construction project. They can take the Developer’s business logic—the "furniture"—and simply drop it into the pre-assigned rooms. Because the environment is already defined, the application inherits the security posture of the blueprint immediately. There is no retrofitting. There is no "I forgot to close port 80." The security is in the DNA of the deployment.
The Engine Under the Hood: Korvette-S WoSPs
How does a static blueprint enforce active security? The secret lies in the Korvette-S Workload Security Proxies (WoSPs).
In a Lane7 deployment, every application container is paired with a WoSP sidecar. If you are familiar with the concept of a sidecar in Kubernetes (like Envoy in Istio), the architecture will seem familiar, but the function is distinct.
The WoSP is the bodyguard for the application. It intercepts all traffic going in and out of the application container. But unlike a standard proxy that just routes traffic, the Korvette-S WoSP performs rigorous zero-trust enforcement and networking functions.
When App A tries to talk to App B, it doesn't talk directly. App A talks to its WoSP. That WoSP talks to App B's WoSP. They verify credentials, check authorization defined in the blueprint, and only then allow the data to pass.
Crucially, this happens efficiently and automatically. The Platform Engineer, DevOps, and Developer don’t write code to talk to the WoSP; the blueprint handles the injection. This separation of concerns means the application logic remains pure, while the network logic remains robust.
Five Pillars of the Lane7 Advantage
This approach—Network First, powered by blueprints and WoSPs—delivers distinct advantages that solve the specific headaches of modern security leaders. Let's break down the four key differentiators.
1. Zero Trust Without the PKI Nightmare
The Problem: In traditional service meshes, achieving Zero Trust (where no traffic or traffic source is trusted by default) usually relies on Mutual TLS (mTLS). mTLS requires a Public Key Infrastructure (PKI). You have to issue certificates to every service, rotate them before they expire, and revoke them if they are compromised. Managing PKI at the scale of thousands of ephemeral containers is an operational heavy lift that breaks many teams. And the automated PKI systems, moving at cloud speed, are unable to meet a very important Zero Trust principle: verification of trust at every transaction.
The Lane7 Difference: Lane7 achieves Zero Trust without the complexity of traditional PKI management. Because the blueprint pre-configures the identity of every workload, the WoSPs can rotate their credentials (ephemeral identity and secret credentials) that are observed and verified automatically in runtime..
We eliminate the "certificate hell." You get the cryptographic assurance that Service A is allowed to talk to Service B, but you don't inherit the administrative burden of being your own Certificate Authority. It is Zero Trust that is actually usable.
2. Security by Design: Pre-Configured Authorization
The Problem: In a standard K8s deployment, security is often "allow all" by default inside the cluster. Developers have to manually write NetworkPolicies to restrict traffic. This is a blacklist approach—everything is allowed unless I say stop. It is prone to human error; one missed policy leaves the database exposed to the frontend.
The Lane7 Difference: Lane7 operates on a whitelist model via Security by Design. The blueprint dictates the relationships. If the blueprint doesn't say the Frontend can talk to the Database, it cannot.
This authorization is pre-configured in the design phase. It isn't a firewall rule patched on later; it is an architectural constraint. By defining the allowed pathways before the application is deployed, we eliminate the possibility of "drift" where an application accidentally exposes an endpoint it shouldn't. The security architecture is the application architecture.
3. Security by Default: Cloud Native AMTD
The Problem: Most security tools are reactive. They look for known bad signatures (Anti-Virus) or anomalous behavior (IDS/IPS). They are static defenses against dynamic attackers. If an attacker finds a vulnerability, they have infinite time to exploit it because the target (with static access credentials, such as API keys) never changes.
The Lane7 Difference: This is the game-changer. Lane7 includes Automated Moving Target Defense (AMTD) at runtime.
Through the Korvette-S WoSPs, the access credentials are not static. The "doors" and "locks" of the services shift. It’s like trying to rob a bank, but the front door moves every ten seconds and the lock changes shape every five.
This provides Threat Rejection. Even if an attacker gets into the network, they can see traffic but cannot access a target workload because the needed credentials are constantly moving. This is Security by Default. The user doesn't have to toggle a "Turn on AMTD" switch; it is inherent to the runtime environment of the blueprint. We move from hunting threats to simply invalidating them.
4. Simplicity: The One-Line Deploy
The Problem: We touched on "YAML Hell." Deploying a secure, meshed microservices app usually involves a folder containing 50+ files: Deployments, Services, Ingresses, ConfigMaps, Secrets, VirtualServices, Gateways. A typo in file #42 brings the whole system down.
The Lane7 Difference: Lane7 Blueprints encapsulate all this complexity into a single, well-documented zip bundle.
Because the blueprint is pre-integrated, the Kubernetes manifests are pre-generated, configured, and validated. The user only needs to unzip the bundle. They can deploy the entire application network—infrastructure, security policies, and routing logic—with effectively one line of code!
This democratization of deployment means that a junior developer can deploy a banking-grade secure network without needing to be a Kubernetes expert. It removes the "tribal knowledge" bottleneck where only one person in the company knows how the deployment script works.
5. Velocity: From Days to Minutes
The Problem: In the traditional model, setting up a new environment for a secure application is a project. Provisioning the cluster, installing the mesh, configuring the certificates, setting up the ingress, and testing connectivity can take days or weeks.
The Lane7 Difference: By front-loading the architectural decisions into the Blueprint, we achieve massive acceleration.
We are seeing application network deployment times drop from days to less than 30 minutes. In some streamlined use cases, we are seeing full deployments in as little as five minutes.
This is not just about saving time for the initial install. This is about disaster recovery. It’s about spinning up ephemeral test environments. It’s about the ability to tear down and rebuild your entire infrastructure in the time it takes to get a coffee. When the network is a pre-packaged commodity rather than a bespoke craft project, velocity becomes the new normal.
The Architect as DevSecOps Enabler
For too long, security architects have been viewed as the "Department of No"—the gatekeepers who slow down deployment to ensure safety. The Lane7 approach changes this dynamic.
By using Blueprints, the security architect becomes a co-enabler with their DevOps and Platform Engineering team, bringing a new vitality to DevSecOps. You provide the development team with a pre-secured, pre-wired environment. You tell them, "Go as fast as you want, because the guardrails are already built into the track."
We are moving away from the era of manual configuration and reactive patching. We are entering the era of the Application Network First. By securing the blueprint, we secure the future.
Try a Lane7 Blueprint for Free!