Zero Trust Without the
"Complexity Tax"
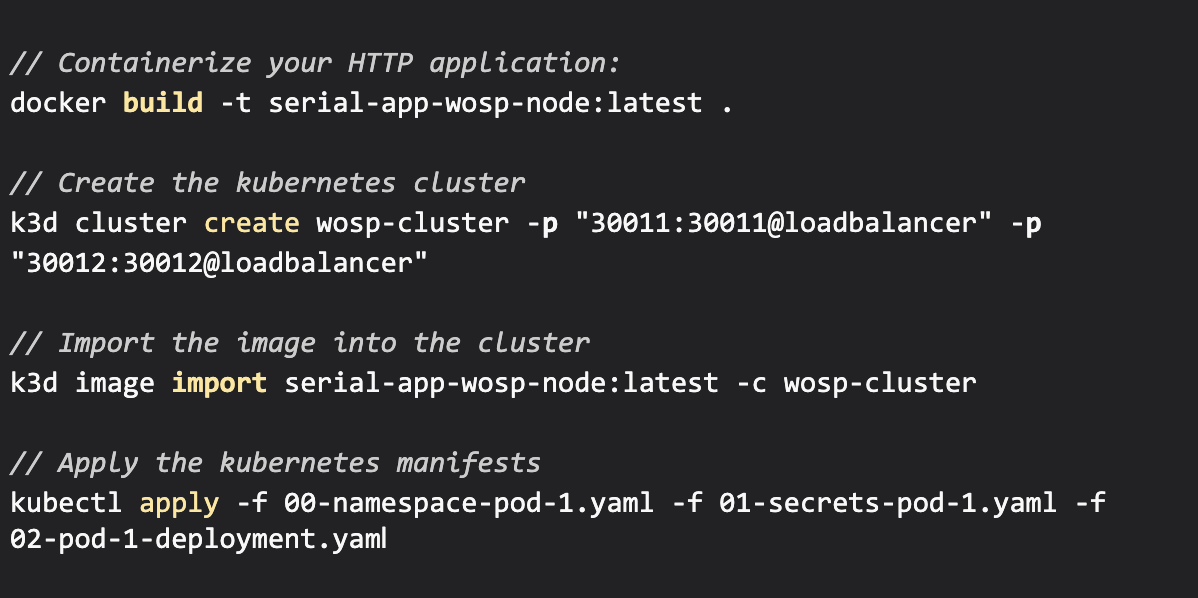
Stop wrestling with complex service meshes, brittle mTLS configurations, and manual certificate rotation. Get security-as-code with a lightweight Envoy sidecar that just works.
Lane7 blueprints simplify and accelerate the deployment of Zero Trust application networks